SOC 2 Compliance For AWS
Configure, Monitor, and Maintain SOC 2 Certification In Amazon Web Services
SOC 2 Compliance In AWS
SOC 2 is a reporting framework that defines security criteria for managing client data, and is developed by the American Institute of CPAs (AICPA). Enterprise organizations, especially in regulated industries often utilize SOC 2 reports as a measure of security preparedness and validation for SaaS solutions and outside vendors. Companies may ask vendors for a current SOC 2 Type 1 or SOC 2 Type 2 report during procurement and security assessment.
Under the AWS cloud shared responsibility model, AWS is responsible for many of the physical compliance safeguards. It is up to the AWS cloud customer to implement administrative policies, set internal security controls and go through a SOC 2 audit with an independent third-party to receive SOC 2 Type II report.

Custom Compliance Policies
SOC 2 requires that organizations set security policies and address safeguards including managing availability, creating data security controls and managing incident response. Dash enables teams to generate custom compliance policies based around on your organization’s needs, structure, and technologies. Policies are designed around Amazon Web Services and customized to streamline SOC 2 Type I and SOC 2 Type II reports.
Learn More About Administrative Policies
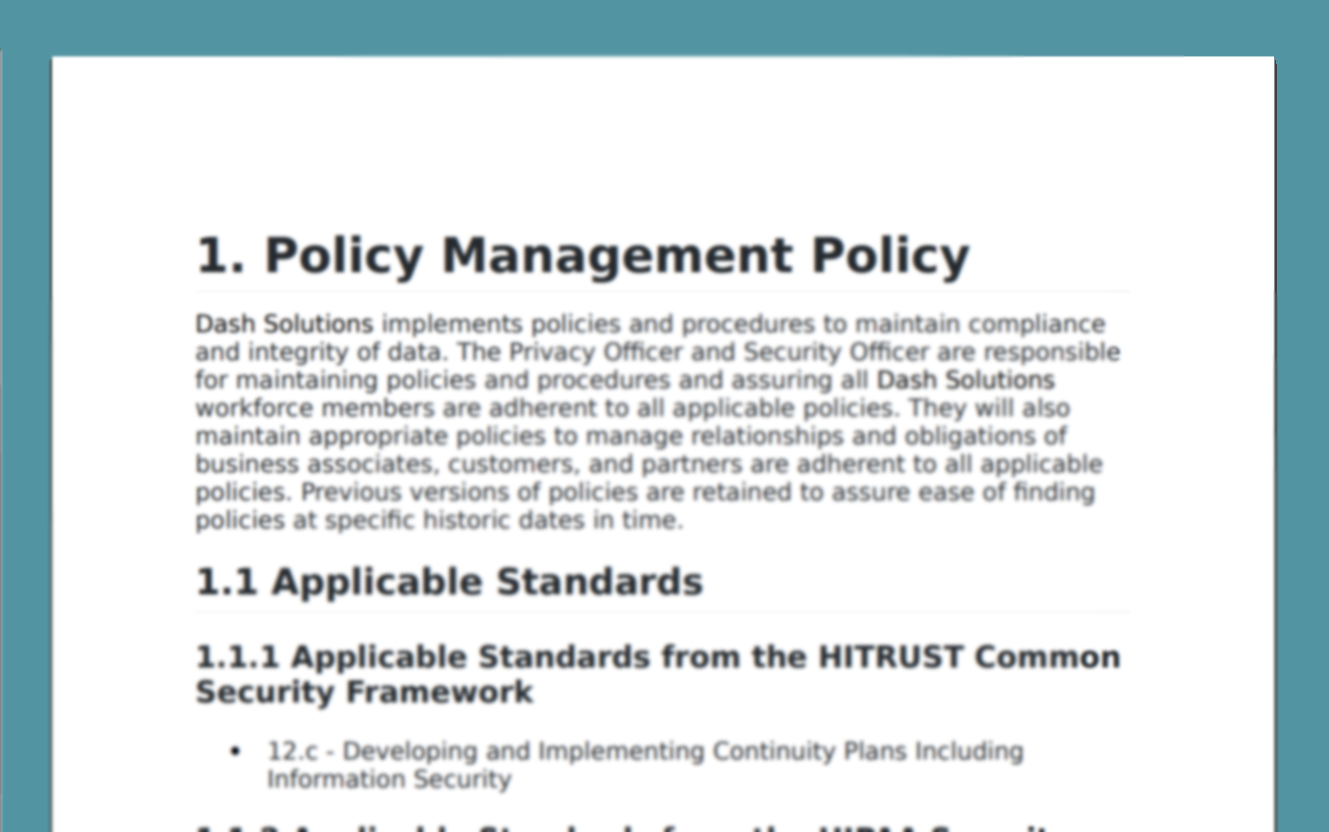
SOC 2 Internal Security Controls
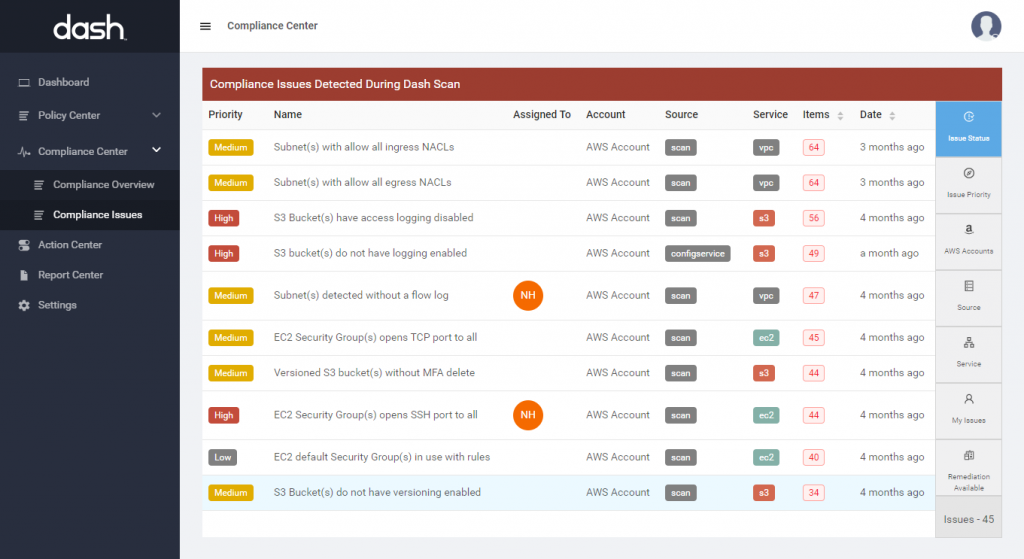
Dash establishes a set of SOC 2 internal controls based around your organization’s established policies and procedures. Security controls are built around individual AWS cloud services, best security practices, and the latest AICPA 2017 SOC 2 Trust Service Criteria (TSC) and aligned security controls. Organization can utilize Dash “click-to-fix” remediations to resolve compliance issues with one click and maintain technical security standards.
Learn More About Technical Controls
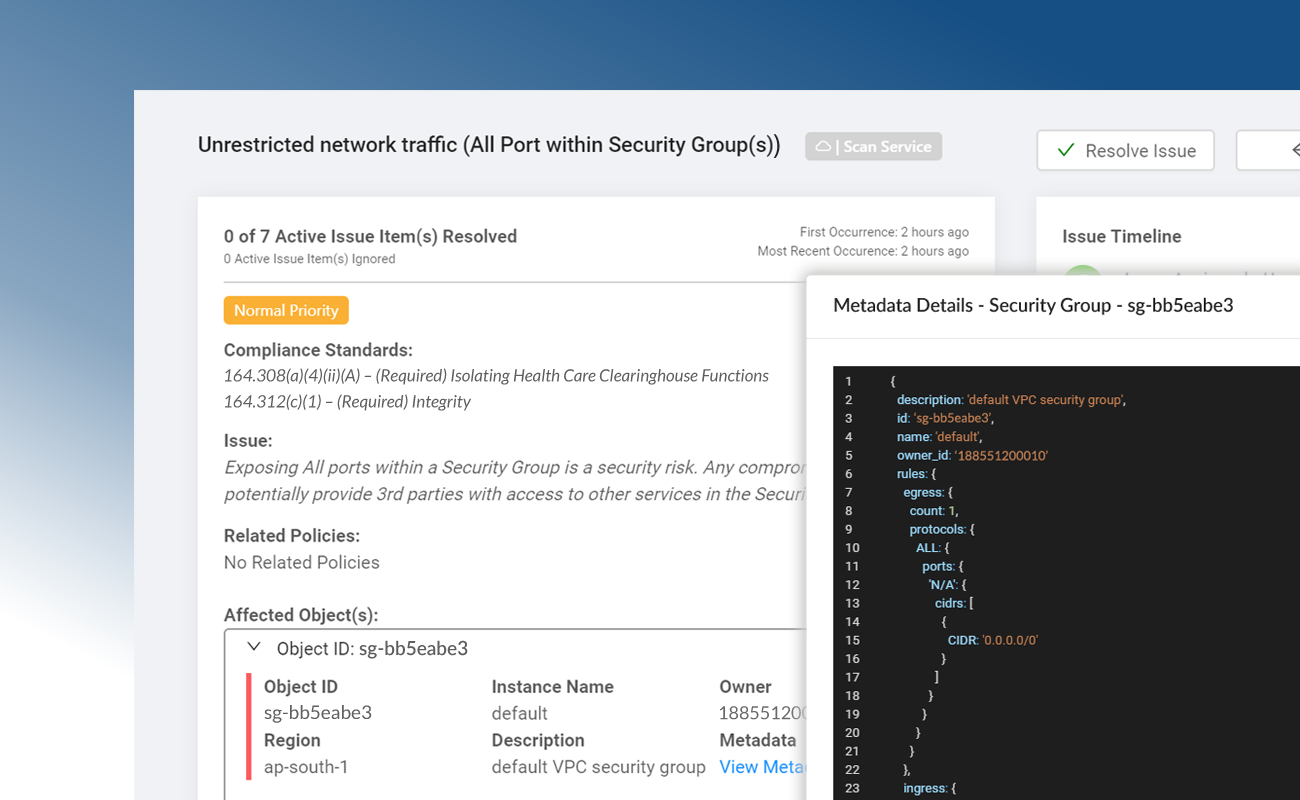
Monitor and Maintain Controls For SOC 2 Type II
SOC 2 Type II requires service organizations to validate internal controls over a period of time, typically 6 to 12 months. Dash makes it easy to continuously monitor and maintain SOC 2 internal security controls across your AWS accounts. Dash detects SOC 2 compliance concerns in your cloud environment such as unencrypted EBS volumes, audit logging issues and S3 buckets that are open to the public, alerts your team, and provides steps for resolving issues before they become full-blown violations.
Learn More About Continuous Compliance Monitoring
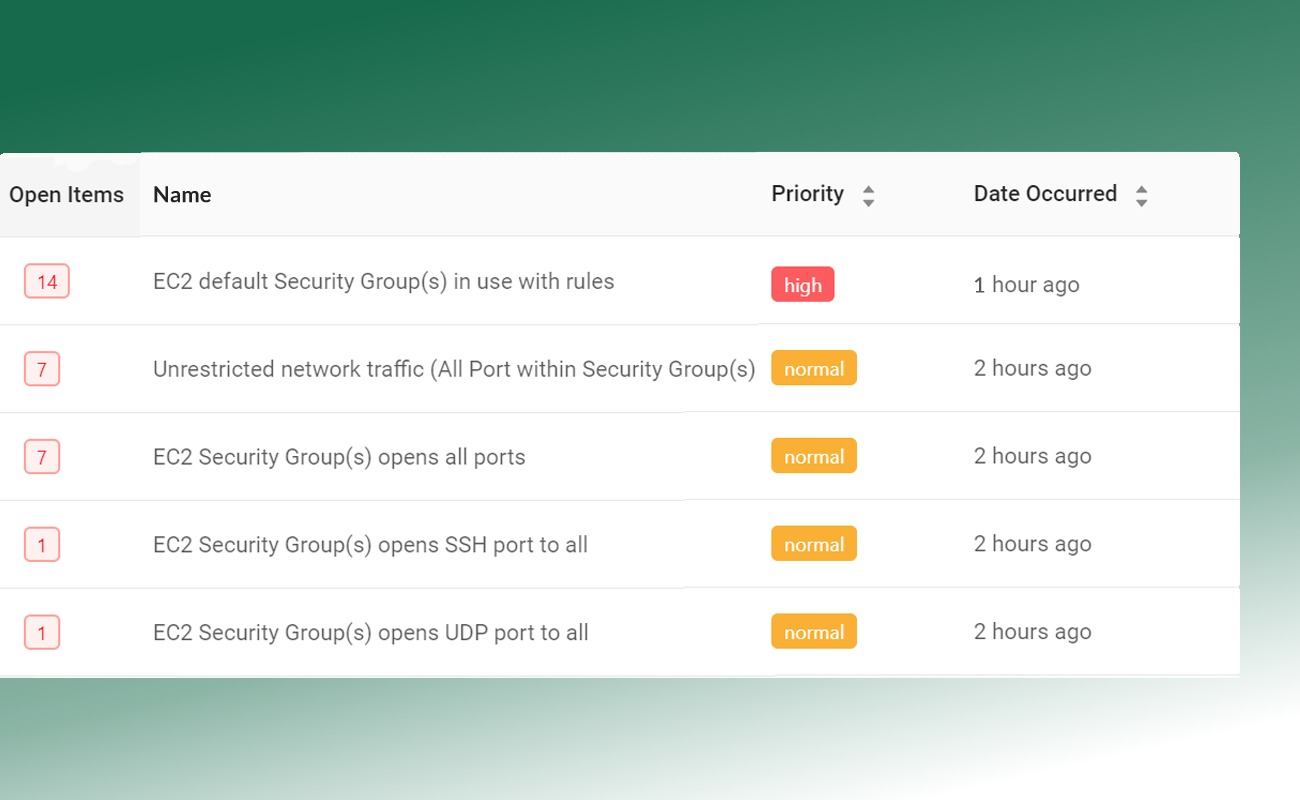
How Do You Achieve SOC 2 Type 2 For AWS?
Prepare Security Program
Organizations should establish a SOC 2 security program that addresses Trust Services Criteria. Teams should develop administrative policies, implement cloud security controls, and gather all security evidence and documentation to prepare for an audit.
Perform A SOC 2 Audit
Organizations must engage with a third-party audit firm to perform a SOC 2 audit. Teams should consider selecting a reputable firm that has worked with similar clients and security expertise.
Maintain SOC 2 Controls
After receiving a SOC 2 report organizations must continue to maintain SOC 2 internal controls across their AWS cloud environment. Teams must complete a SOC 2 audit every year in order to stay current with their SOC 2 report.

Get Started With AWS SOC 2 Automation.
Address SOC 2 Trust Service Criteria (TSC) In AWS
Dash enables teams to build and implement compliance controls around SOC 2 Trust Service Criteria and streamline the process for preparing for SOC 2 audit and certification.
Security
The Security principle refers to how system resources are protected against unauthorized access. This principle includes implementing necessary access control, network firewall, intrusion detection systems (IDS).
Availability
The Availability principle refers to the accessibility and availability of systems and core services within the organization, as well as contract and service level agreement (SLA) standards. This principle includes standards around building highly available systems, addressing service failover, resource monitoring, and contingency plans.
Processing Integrity
The Processing Integrity principle refers to the ability of systems to deliver accurate data. Data processing must be accurate, timely, and authenticated. For organizations this includes managing data integrity and setting quality assurance processes for managing data.
Confidentiality
The Confidentiality principle refers to the access and disclosure of data to authorized parties. This includes implementing standards around access control, user roles, network firewalls, and transmission encryption.
Privacy
The Privacy principle refers to system collection, use, and retention of personal information in relation to organization’s privacy policies. Security controls must be implemented to protect Personally identifiable information (PII).
Achieve SOC 2 Type II in Amazon Web Services
Prepare For a SOC 2 Audit In AWS
Dash enables teams to plan and implement internal controls in AWS and achieve SOC 2 certfication
Determine Gaps and Set Policies and Security Controls With Dash
Dash ComplyOps makes it simple for your team to identify SOC 2 security gaps across AWS and implement proper security controls.
Dash enables teams to create custom administrative policies mapped to the latest SOC 2 trust service criteria and enforce controls through continuous compliance monitoring.
Dash allows teams to:
- Define SOC 2 necessary administrative security policies
- Set AWS cloud security controls for SOC 2
- Monitor and enforce security standards across your cloud environment
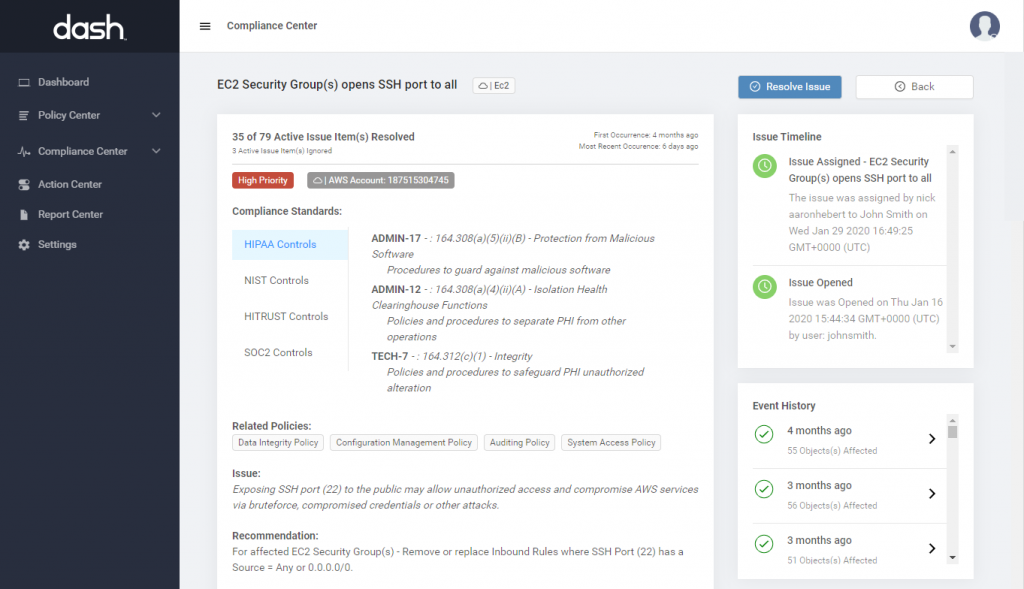
Inventory SOC 2 Security Controls
Teams should collect all relevant documents, security evidence and agreements. Teams should consider gathering the following security evidence for assessment:
- All current administrative policies
- AWS SOC 2 report and security attestations
- Agreements with vendors and third party contractors
- Evidence for all security mappings and implemented security controls
Dash automatically creates an inventory of SOC 2 security controls and collects all security evidence necessary for your SOC 2 audit.
Complete SOC 2 Audit

Once your team has gone through the Dash SOC 2 readiness process, and has implemented all necessary security controls, your team can work with our established SOC 2 auditing partner to complete a SOC 2 audit.
Teams will work with the auditor to evaluate the effectiveness of internal controls and receive SOC 2 type 1 or SOC 2 type 2 report. Organizations can use this SOC 2 report as security validation to share with partners and clients.
Build Your SOC 2 Security. Program
AWS Focused Compliance Solution
Dash enables organizations to build a robust security plan and security controls for Amazon Web Services
AMI Deployed
Dash is deployed into your AWS Cloud account and allows teams to manage cloud services.
Utilize 100+ Cloud Services
Dash can be used alongside the hundreds of AWS cloud services to rapidly build, manage and get-to-market.

Streamline SOC 2 Compliance In The Cloud
Automate SOC 2 Controls and Achieve SOC 2 certification for Amazon Web Services