Create SOC 2 Administrative Policies & Controls
Dash ComplyOps makes it easy for your team to build and manage your organization’s SOC 2 security program.
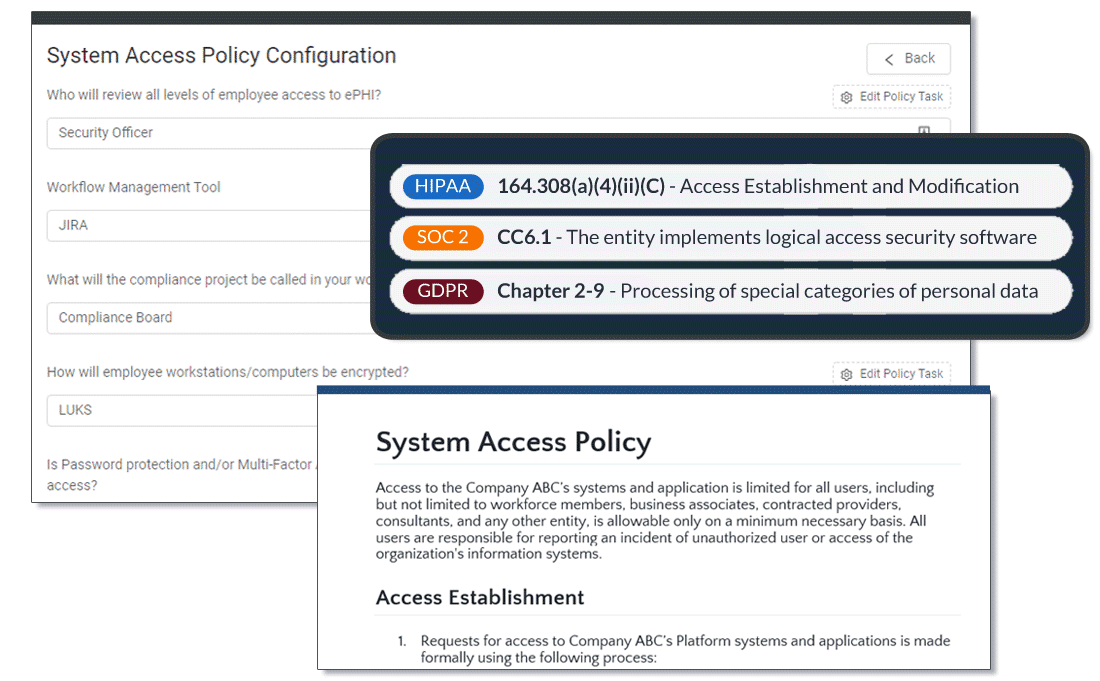
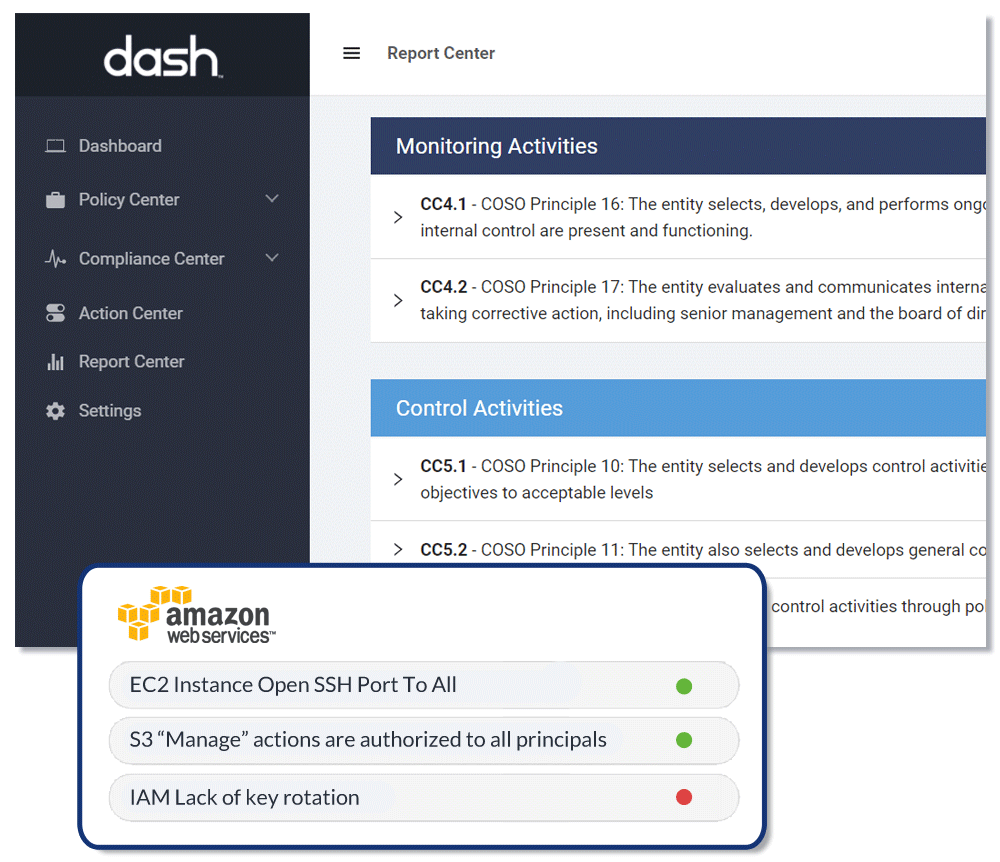
Dash enables teams to build custom administrative policies mapped to SOC 2 Trust Service Criteria (TSC) requirements and enforce controls through continuous compliance monitoring.
- Define Required Administrative Security Policies
- Implement Safeguards For SOC 2 Service Criteria
- Monitor and Enforce Policies & Controls Across Your Cloud Environment