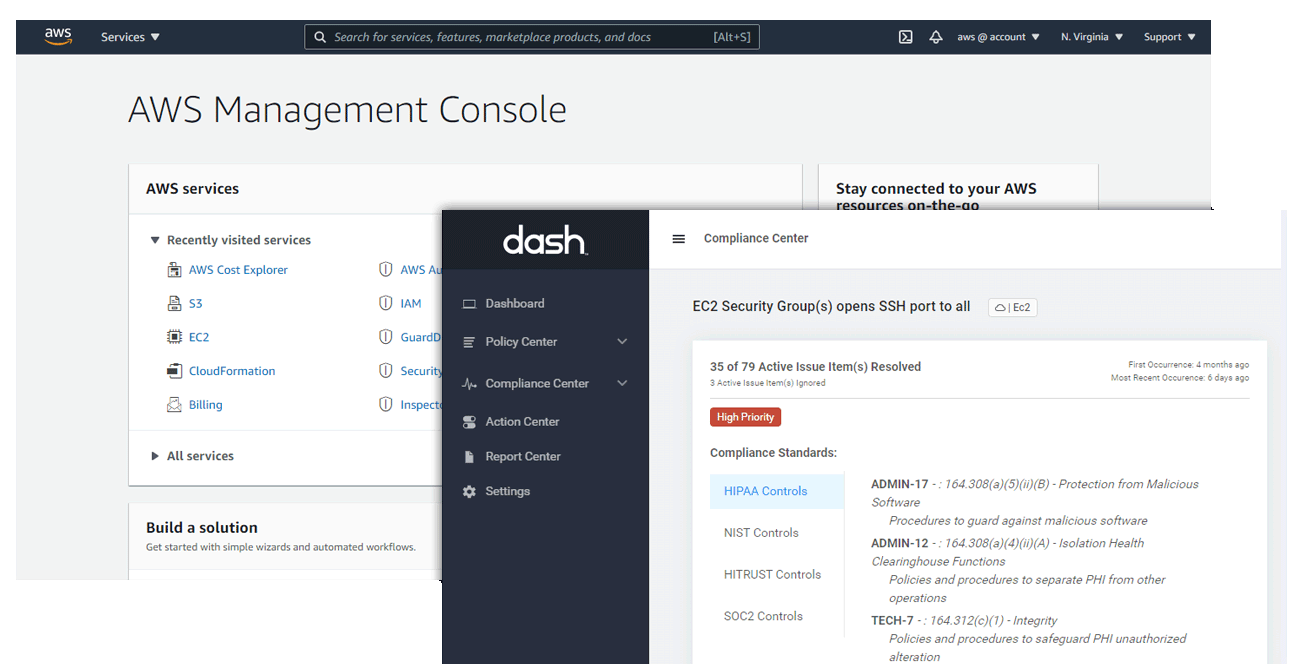
Cloud security posture management (CSPM) is a key piece in Cloud Security, and a must for any cloud-based business. With CSPM, your team can visualize and assess risks, check your compliance against different security frameworks, and ensure you’re applying cloud security best practices.
CSPM enables teams operating in public cloud platforms such as Amazon Web Services (AWS) to monitor and maintain specific security and configuration settings across their IT infrastructure and cloud environments. CSPM can be a vital part for Service companies (IaaS), Software as a Service (SaaS) companies, and Platform as a Service (PaaS) companies, and can save DevOps teams hundreds of hours a month.
But, what is CSPM exactly? When do you need CSPM? Who can help you get started?
Let’s find out.
What Is CSPM?
Coined by Gartner, the term Cloud Security Posture Management, or CSPM, refers to multiple IT security tools. These security tools are all designed to find potential security risks and misconfiguration issues in your cloud-based platform (AWS, Azure, etc).
A CSPM solution is typically designed to monitor a cloud infrastructure around the clock, and let users know as soon as a potential security issue arises. Security teams can then make sure any misconfiguration issues are resolved.
Some CSPM tools will merely alert the cloud customer of the need of fixing a risk or potential risks. More advanced CSPM tools can provide robotic process automation, or RPA, to automatically fix most issues, and simplify the process for the cloud customer.
What Causes Cloud Misconfigurations?
Misconfigurations are usually caused by several issues. The main cause of cloud misconfigurations is the lack of awareness of cloud security and policies, closely followed by the lack of adequate controls and oversight.
Teams that do not have strict cloud security standards may end up deploying resources that are unencrypted, do not have audit logging enabled or have network settings that are open to the public. Cloud platform users may also accidently modify or change a resource’s security configuration.
Consider the following causes of cloud misconfigurations:
- The public cloud is inherently programmable, easily allowing cloud users to make infrastructure changes.
- New cloud technologies may be harder to manage or have a security configuration options that security teams are unfamiliar with.
- Enterprise environments can become too big or complex to keep track of. This issue is particularly relevant in larger cloud infrastructures, with a large volume of resources and accounts.
If misconfigurations are not resolved, cloud resources can be exploited or become compromised. The longer serious misconfigurations are undetected, the more challenging they may be to fix, and the more likely your platform is to risk a security breach.
When Do You Need CSPM?
Since cloud environments can have thousands of resources, which can be altered by many different users or services, it can be difficult for organizations to manage overall security settings and configuration. Traditional security solutions are not designed to protect your cloud and cloud security can be a challenge to organizations with limited DevOps and SecOps resources.
Teams turn to CSPM solutions in order to streamline the cloud security process. If your team is manually managing your organization’s cloud security programs, you may want to consider a CSPM tool to help your team protect your cloud environment and maintain robust security standards.
CSPM tools such as Dash ComplyOps can help teams ensure continuous compliance with a number of standards, like HIPAA and SOC 2 and can even reduce the time and resources spent fixing issues through automated remediation.
Automating Configuration Management & Cloud Security
If your organization is automating or streamlining configuration management for production services, it may make sense to implement a CSPM system. A CSPM solution helps your team to monitor and maintain high cloud security standards and provides insight for updating your configuration management systems and security runbooks.
Managing Regulatory Standards and/or Cybersecurity Frameworks
If your organization operates in a regulated industry such as Healthcare or Financial Services, your company must comply with specific regulatory standards such as HIPAA/HITECH, PCI DSS, and FedRAMP and cybersecurity frameworks such as SOC 2 and ISO 27001. In order to ensure that your cloud security standards and security posture meets regulatory compliance, your team may consider implement a CSPM system.
Validating Security Programs to Enterprise Clients & Partners
Organizations and software vendors providing solutions to large enterprises or Fortune 500s are often subject to security risk assessments (SRAs) and security questionnaires during the procurement process. Managing robust security standards through a CSPM solution provides clients and partners with evidence that your team takes security and compliance seriously and is a reputable partner.
Getting Started With CSPM
Looking to get started with CSPM? Here’s how to get started, step by step:
Step 1: Set Security Goals
It’s hard to remove a threat if you aren’t even aware it even exists. Your team should analyze your security goals and determine where a CSPM, fits in the overarching security strategy. Your may consider how your team utilizes the cloud, manages deployments, and enforces cloud security standards
Spend time with your team determining cloud security issues that need solving, deciding on the solution and its manager, and define success from the beginning.
Step 2: Select A CSPM Solution
Balance the pros of cons of each potential tool and solution, and how they may approach cloud security. A CSPM tool like Dash ComplyOps can help your proactively find issues through continuous compliance monitoring and solve issues without user input. Your team should consider potential configuration management and processes, when selecting a solutions
Get in contact with CSPM vendors and evaluate how their offering fits into your overall security program.
Step 3: Implement A CSPM
Cloud security is managed by more than one team member. Your team should make sure all relevant users are adopting and utilizing CSPM and cloud security standards as part of your overall cloud operations.
Continue tracking your cloud security controls and checking the effectiveness of your cloud security program and connected CSPM.
Step 4: Keep Testing and Improving Your Security Program
As your organization and infrastructure changes so will your cloud environment. Ensure that your team reviews all cloud security controls and updates security policies on an ongoing basis. Review CSPM findings and update CSPM settings to meet your changing infrastructure needs.
Your security team should continually review security findings and test the overall response and processes regarding your response to the new security findings.
Build Your Cloud Security Posture With Dash ComplyOps
Dash ComplyOps provides security teams with a cloud security posture management (CSPM) solution for creating custom policies and enforcing policies and security controls across AWS cloud environments.
With Dash, teams can easily adopt cybersecurity standards such as HIPAA, SOC 2, and ISO 27001. Dash enables teams to enforce security controls and ensure that all cloud configuration is in-place for cloud settings including encryption, access control, audit logging, and backup and disaster recovery (DR), etc.
Learn how Dash ComplyOps can help your team build and maintain a secure cloud security posture.