The Health Insurance Portability and Accountability Act, or HIPAA defines a set of security protections for managing patient data. With many healthcare organizations and software vendors moving into the public cloud, security and HIPAA compliance is more top of mind. Healthcare providers and organizations selling solutions into the healthcare industry must ensure that they are following all HIPAA physical, technical, and administrative safeguards when building solutions that will interact with patient data.
Fortunately, Amazon Web Services (AWS) can be utilized to build HIPAA compliant solutions in the cloud. AWS has many established security programs and allows healthcare organizations to jump start their compliance programs, but organizations must manage specific security safeguards in order to use AWS and be HIPAA compliant. Below is a list of best practices and specific steps security teams should consider when building HIPAA compliant applications in AWS:
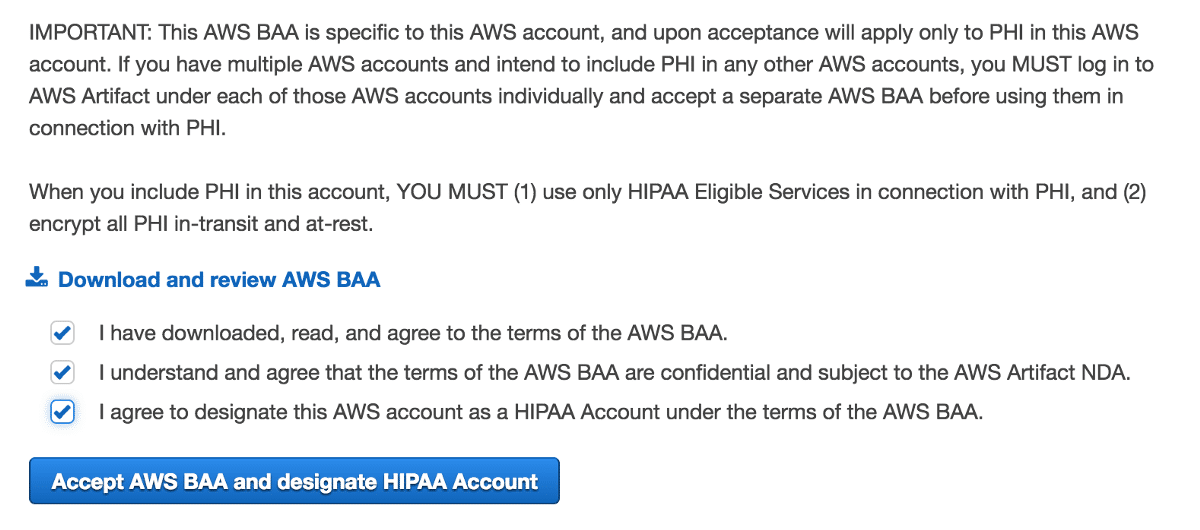
1. Sign a Business Associates Addendum (BAA) with AWS
Before storing or managing any PHI in AWS, organizations must sign and execute a Business Associates Addendum (BAA) with Amazon Web Services. Most public cloud platforms, including AWS operate on a cloud shared responsibility model. Under this model, security and compliance responsibilities are shared between the cloud service provider and the cloud customer. The AWS BAA agreement dictates specific security safeguards provided by AWS and security responsibilities your organization’s must manage.
2. Implement Administrative Policies Based Around Your Organization
Organizations building HIPAA compliant solutions in AWS, must implement all necessary administrative policies and safeguards in order to comply with HIPAA regulations. Security teams should build security policies and standard operating procedures (SOPs) that address HIPAA administrative requirements. Policies should include plans for incident response, backup and disaster recovery (DR), employee training, risk assessment, and compliance roles. It is important that policies focus on building policies that will be properly followed within the organization. Administrative policies should be reviewed on a periodic basis and be updated to reflect organizational changes and technology changes.
3. Utilize Only AWS “HIPAA-Eligible” Services with PHI
The AWS Business Associates Addendum (BAA) provides a list of AWS cloud services that are “HIPAA eligible” or may be used with PHI. In order to maintain HIPAA compliance in AWS, organizations may only utilize PHI with AWS HIPAA eligible services. Teams should ensure that PHI is stored, managed, and/or processed on HIPAA covered services. Cloud services not on the HIPAA eligible services list should not be used with PHI.
Utilizing HIPAA eligible services does not automatically make AWS HIPAA compliant. Your organization must implement security controls for individual AWS services. You can learn more by reading our guide to Planning and Architecting for HIPAA Compliance.

4. Encrypt all PHI data “In-transit” and “At-rest”
HIPAA requires that all PHI is encrypted when “at-rest” and “in-transit”. Organizations utilizing AWS infrastructure should ensure that encryption is enabled for cloud services such as EC2 volumes, S3 buckets, and RDS clusters and storage. Additionally, PHI should be encrypted “in-transit” using SSL/TLS standards and forcing an encrypted connection when possible with cloud services.
S3 Buckets security configuration around client-side and server-side encryption can be utilized to create a HIPAA compliant configuration for Amazon S3.
5. Collect Security Events and Audit Logs
HIPAA requires that organization implement audit logging to detect potential security issues and malicious behavior. Organizations should plan to collect audit logs and security events from cloud applications and services. Teams should collect cloud access logs – such as S3 access logs, RDS access logs, and other individual cloud services. Application logs and security events, such as vulnerability scanning logs and intrusion detection logs should be collected and reviewed on a frequent basis. Teams may consider using AWS services such as Amazon CloudWatch and CloudTrail as solutions for implementing HIPAA compliant audit logging in AWS.
Consider reading the following guide for essential auditing logging for security and compliance in AWS.
6. Implement Proper Access Control and Authentication
Access Control and Authentication controls must be implemented to comply with HIPAA. Organizations managing HIPAA compliance in AWS need to ensure that cloud services are locked down and access to PHI is provided to only necessary staff and users. Teams should utilize Amazon IAM users and roles and set permissions in order to AWS user limit access to appropriate services. Organizations should also define a robust AWS password policy and remove temporary and outdated user roles on a periodic basis.
Organizations can see the following Dash HIPAA security guides for Amazon EC2 and Amazon S3 and configuring HIPAA security controls for individual AWS services.
7. Monitor Security and Compliance Going Forward
Managing AWS HIPAA Compliance is not a one-time process. Organizations must continue to follow set administrative policies and ensure that new AWS cloud infrastructure is configured in a HIPAA compliant manner. As new cloud services are provisioned and new staff are added, HIPAA compliance can becoming increasingly more complex. New AWS resources may be misconfigured and may fall out of compliance, and “organizational drift” can occur when security policies change and cloud resources do not meet compliance standards.
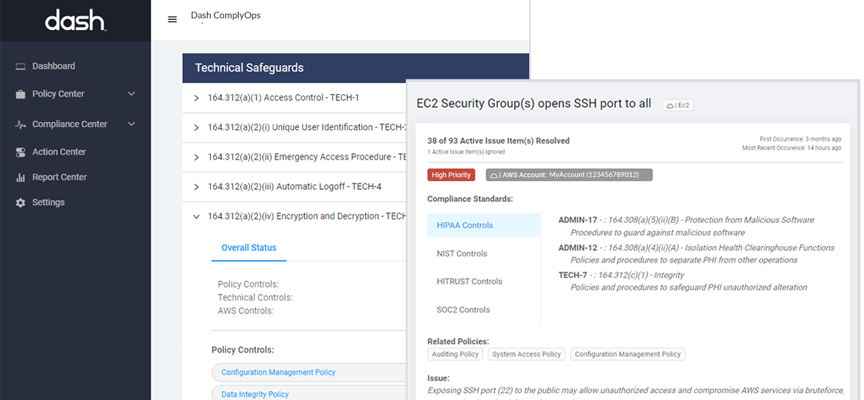
Having standard operating procedures makes this process easier. Dash ComplyOps continuous compliance monitoring provides security teams with a platform for easily identifying cloud security issues, and resolving AWS HIPAA compliance issues.
While AWS provides a wide array of cloud services and security configuration options, it is important to recognize that organizations must handle specific security processes in order to be HIPAA compliant. Healthcare organizations must ensure they implement all necessary administrative and technical safeguards when building healthcare applications on AWS and managing HIPAA compliance.
The above steps good first steps for achieving HIPAA compliance in AWS. Dash ComplyOps provides organizations with a platform for creating custom HIPAA security policies and implementing technical security and controls. Dash continuous compliance monitoring enables teams to identify and resolve cloud compliance issues before they become potential HIPAA violations. Dash is easily installed in your cloud environment and can be easily deployed from the AWS Marketplace.
Learn how Dash can help streamline HIPAA compliance in Amazon Web Services.




