How To Achieve SOC 2 Compliance?
A Complete SOC 2 Type 2 Guide & Certification Overview
No time to read?
Save our SOC 2 Type 2 guide and read it later
(Valuable checklists included!)
Download SOC 2 Guide & Included Checklists

- PDF SOC 2 Guide
- SOC 2 Getting Started Checklist
- SOC 2 Audit Guidance
More and more users are concerned with data security. The best way to validate security postures is SOC 2.
In this article, we’ll go through how to achieve SOC 2 compliance and answer some common questions. We’ll also talk about information like:
- Why is SOC 2 important
- Who needs SOC 2
- How to maintain SOC 2 compliance
- …and much more
By the end of this article, you’ll know all the essential information about SOC 2 compliance, who needs it, how to achieve it, and why.
Let’s get started.
What is SOC 2?

SOC 2, stands for System and Organization Controls 2, and is a complex auditing framework developed by the American Institute of Certified Public Accountants (AICPA). SOC 2 is a highly popular auditing procedure that stands for System and Organization Controls 2.
That way, you can make sure you can protect the owners of that data, like your users and your company itself.
SOC 2 reports provide valuable insight into:
- Oversight of the organization
- Vendor management programs
- Internal corporate governance and risk management processes
- Regulatory oversight
Unlike laws and regulatory standards like HIPAA, PCI DSS, or SOX, you don’t legally need to comply with SOC 2.
Instead, SOC 2 stands as a voluntary auditing standard that you can adopt to validate and prove your security posture.
Since it’s voluntary, it says a lot about security when a company complies with SOC 2.
What Are The Types Of SOC 2 Reports?
There are two types of audits and SOC 2 reports that can be conducted for SOC 2 – Type 1 and Type 2:

SOC II Type I
An audit and report on an organization’s system and design of its security controls related to the Trust Services Criteria (TSC).
SOC II Type II
An audit and report on an organization’s system and design of its security controls related to the Trust Services Criteria (TSC) and operating effectiveness of controls.
What’s the Difference?
A SOC II Type 2 audit includes all the same information as Type 1 but also features the auditor’s assessment that the organization’s controls have been tested for effectiveness over a period of time. An organization is typically evaluated for a 6 month period or longer to assess that internal controls are in place.
While SOC 2 Type 1 Reports do provide some initial security validation, the value of a Type 1 diminishes as the report gets older, since internal controls are not evaluated over time.
That’s why many organizations work to achieve and keep a current SOC 2 Type 2 report to prove that internal controls are current.
Why Be SOC 2 Compliant?
Data security is becoming more and more important for companies and regulated industries, organizations. That’s why you can see them turning to audit standards like SOC 2 so they can validate organization security postures.
If your company is working with large enterprises or with sensitive data in regulated industries, getting compliant now will help your team strengthen your security posture, validate your security processes, and streamline security assessments and procurement.
Sellers and companies work to be SOC 2 compliant to achieve the following reasons:
- To strengthen their overall security programs and lower the potential risk of a security breach.
- To provide a level of security validation, like the stamp of approval SOC 2 provides, which makes it easier to go through enterprise procurement and security review.
- To meet a company or prospect’s requirement of achieving SOC 2 certification.
44% of Enterprises Have
Experienced A Data Breach
as a direct result of an
insecure third-party vendor.

Who Should Be SOC 2 Compliant?
The obvious candidates for SOC 2 compliance are companies operating in regulated industries, like healthcare, finance, and any other company that needs to meet stringent security standards or face large monetary penalties.
Large companies must also make sure that new sellers and software solutions have established security programs and do not pose a risk to the organization.
Why?
Because 44% of enterprises have experienced a data breach caused by a vendor.
If you also take into account the increasing importance and usage of digital data, it’s easy to see why security assessment and validation is quickly becoming a bigger focus.
How To Achieve SOC 2 Certification – 5 Steps
If you want your organization to achieve SOC 2 certification, you need to prepare for a SOC 2 audit.
Your security teams need to establish security controls, engage with a reputable audit firm, and validate the effectiveness of security standards within the organization. Your teams should outline a roadmap for building their security programs and working with assessors to resolve security concerns.
Preparing for a formal audit is vital. You can expedite the audit process by gathering and providing appropriate SOC 2 evidence, administrative policies, and technical security standards to streamline the process and making the assessment process as painless as possible.
Here are the 5 steps to achieve SOC 2 Compliance:
1. Approach A Credible Third-party And Determine Gaps
If you want to have an objective assessment and report, your company needs to turn to a reputable third-party to work with for SOC 2 certification. Organizations will work with these stakeholders to determine gaps in their security programs.
Oftentimes an organization will perform a SOC 2 scoping and readiness assessment. This exercise acts as a gap assessment and gives security teams a better idea of security controls that require attention or remediation actions.
That’s where companies like Dash come in. With Dash, you can easily create security policies and maintain all necessary security controls with continuous compliance monitoring.
Potential SOC 2 Gaps
Some of the most common SOC 2 gaps are:
- Lack of Formal Administrative Policies
- Undefined Security Roles and Responsibilities
- Lack of Risk Management & Incident Response Plans
- Missing Technical Security or Logical Controls
- Issues with Third-Party Access and/or Confidentiality
2. Select Criteria For Auditing
Next, you need to determine which Trust Services Criteria (TSC) you’ll be assessing. Keep in mind that you may assess one or more categories of criteria.
Security Criteria is a “common criteria” that all organizations must be assessed for when going through a SOC 2 audit. Outside of the Security Criteria, organizations must determine the scope of TSC criteria to be evaluated in a SOC 2 audit.
Since certain control areas and criteria may not apply to the organization, it is up to the team to work with the assessor to determine the scope and value of achieving certification across criteria.
It is up to teams to work with an assessor to determine which criteria are most relevant to the organization and should be measured in an audit.
Descriptions of these criteria and standards are mentioned in this section.
3. Build A Roadmap For SOC 2 Compliance
Once you’ve identified security gaps and security standards that you need to improve, your teams should develop a roadmap for how they’ll implement these security controls.
Audits require precise work and preparation within and outside the organization. Your teams should create a timeline and delegate preparation tasks to appropriate staff members. Staff should review any previous audits that may have been conducted to help identify areas for improvement.
Your teams need to gather data and security evidence ahead of working with an auditor and be available during audit fieldwork. They should have an open line of communication during the audit process, be ready to ask/answer questions and provide additional documentation during evaluation.
Download SOC 2 Guide & Included Checklists

- PDF SOC 2 Guide
- SOC 2 Getting Started Checklist
- SOC 2 Audit Guidance
4. Perform A Formal Audit
After you’ve implemented all necessary SOC 2 security controls to meet Trust Services Criteria (TSC), your organization must schedule a SOC 2 security audit. Your teams will have to answer security questions and provide policies and evidence for security controls.
You should select an audit firm/assessor with the following qualities:
- Experience: The audit firm you choose must have experience in conducting SOC 2 audits, and performed numerous assessments on the latest SOC 2 criteria.
- Project Fit: Your teams should work with an auditor who has worked with similar types of organizations. Your team will receive security insight most applicable to your team, by turning to a firm that has worked with similar-sized companies, industries, etc.
- Good Communication: If you want to avoid any setbacks or confusion, teams should work with auditors that respond to concerns and inquiries within a 24-hour period. Having a good communication loop allows teams to better address issues and progress in the assessment process.
5. Get Certified And Re-Certified
At the end of an audit, if all processes are well-documented and it is determined your team is compliant, you’ll receive the SOC 2 report, otherwise known as a SOC 2 certification.
This report is written by the SOC 2 assessor and outlines your organization’s proficiency with security principles. Teams that work to receive a SOC 2 report can then use that report as a kind of security attestation and validation of the company’s security program.
If you want to maintain certification, your team will have to undergo annual audits to ensure that security measures are properly implemented within your organization.
Dash ComplyOps audit preparation can help your team keep an inventory of compliance controls, automate evidence collection, and help your team achieve audits and certification.
Example SOC 2 Roadmap
- 1. Inventory Vendors and Third Parties
- 2. Set Administrative Security Controls
- 3. Implement Technical Controls
- 4. Perform SOC 2 Audit
- 5. Monitor Security Program
Trust Services Criteria (TSC)
SOC 2 audits vet organizations against a series of Trust Services Criteria (TSC) previously known as Trust Services Principles (TSP). Trust Service Criteria (TSC) are currently outlined in the latest 2017 AICPA Trust Service Criteria TSP Section 100.
The security criteria serve as assessment criteria for reporting on a list of controls that organizations must have implemented in their security programs. Organizations going through a SOC 2 audit may be evaluated on or more service criteria depending on the scope of the assessment and audit.
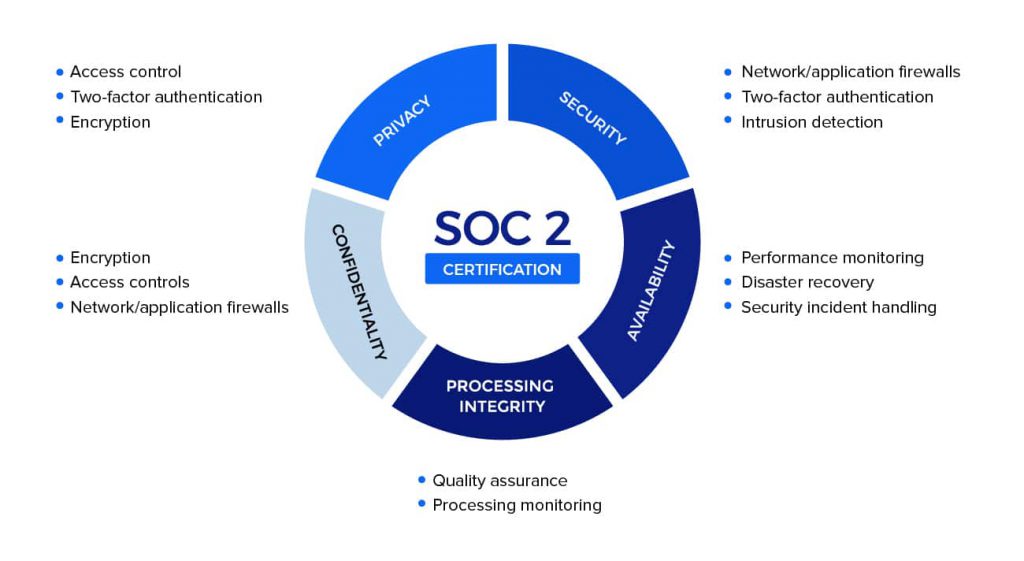
The five Trust Services Criteria (TSC) are:
1. Security
Information and systems are protected against unauthorized access, unauthorized disclosure of information, and damage to systems that could compromise the availability, integrity, confidentiality, and privacy of information or systems and affect the entity’s ability to meet its objectives.
2. Availability
Information and systems are available for operation and use to meet the entity’s objectives. Availability refers to the accessibility of information used by the entity’s systems, as well as the products or services provided to its customers.
3. Process Integrity
System processing is complete, valid, accurate, timely, and authorized to meet the entity’s objectives. Processing integrity refers to the completeness, validity, accuracy, timeliness, and authorization of system processing.
Processing integrity also addresses whether systems achieve the aim or purpose for which they exist and whether they perform their intended functions in an unimpaired manner, free from error, delay, omission, and unauthorized or inadvertent manipulation.
4. Confidentiality
Information designated as confidential is protected to meet the entity’s objectives. Confidentiality addresses the entity’s ability to protect information designated as confidential from its collection or creation through its final disposition and removal from the entity’s control under management’s objectives.
5. Privacy
How personal information is collected, used, retained, disclosed, and disposed to meet the entity’s objectives. Although the confidentiality applies to various types of sensitive information, privacy applies only to personal information.
Additionally, the latest 2017 TSC standards for SOC 2 reports integrate the 2013 COSO framework.
COSO Framework
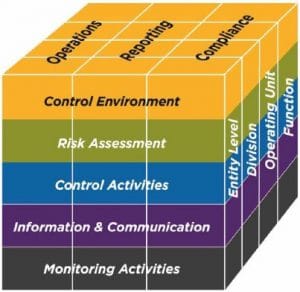
COSO provides a generally accepted framework for internal controls within the organization. SOC 2 integrates the COSO framework including the five components of internal controls:
2013 COSO Framework Components:
- Control Environment
- Risk Assessment
- Control Activities
- Information and Communication
- Monitoring
SOC 2 And The Cloud
Are you using cloud service providers like Amazon Web Services (AWS) to host applications and solutions?
These cloud platforms generally operate on a cloud shared responsibility model for SOC 2 and most compliance frameworks.
This means that, while the cloud provider will handle many of the physical security controls, it is up to you, the cloud customer, to address most administrative standards, and technical security controls to achieve SOC 2 compliance in the cloud.
Administrative Standards
Your company should plan to build a set of administrative policies and standard operating procedures (SOPs) to achieve SOC 2 compliance.
Your security teams should create policies that fit the structure and technology needs of the company.
Administrative policies should address security aspects, including:
- Employee Training
- Incident Response
- Risk Management
- Roles & Responsibilities
- Disaster Recovery
- Configuration Management
Technical Security Standards
While cloud providers give cloud customers many options for security configuration, it is up to your security team to set and enforce SOC 2 controls.
For example, to build and maintain SOC 2 compliance in AWS, your organization must implement the security solutions including:
- Encryption
- Firewall/Networking
- Access Control
- Backup and Disaster Recovery (DR)
- Audit Logging
- Intrusion Detection Systems (IDS)
- Vulnerability Scanning
While many cloud services may be used to implement these security standards, your security team must ensure that policies and cloud security controls are in place.
How To Maintain SOC 2 Compliance
When conducting a SOC II Type II audit, your organization must prove the ongoing effectiveness of your security controls. Additionally, most SOC 2 reports cover a 12-month period, meaning that your organization must complete a SOC 2 audit every year if you want to stay current with SOC 2 compliance.
Due to the ongoing nature of assessments, your company must set proper administrative policies and ensure technical security controls going forward.
Dash ComplyOps enables organizations to streamline collection of security evidence, create security policies, and ensure security controls with continuous compliance monitoring.
Preparing for a SOC 2 audit? Learn how your security team can streamline SOC 2 compliance with Dash and achieve certification quicker.
What About SOC 1 and SOC 3?
While this guide has covered a variety of topics around SOC 2, it is important to note that SOC 2 is part of a series of reports that organizations can achieve to validate organizational controls.
The video below provides a good explanation of the differences between SOC 1, SOC 2, and SOC 3:
Just to recap some of the differences between SOC reports:
SOC 1
A SOC 1 report addresses internal controls that are relevant to a company’s financial reporting. A SOC 1 is designed to review a vendor’s financial and accounting controls.
SOC 2
As mentioned earlier in this guide, a SOC 2 report is an examination of an organization’s controls over one or more of the five Trust Service Criteria (TSC) – Security, Availability, Processing Integrity, Confidentiality, and Privacy. A SOC 2 report details how a vendor manages customer data and handles internal controls.
SOC 3
A SOC 3 report is a security report designed to be made available publicly (without NDA requirements). A SOC 3 will likely have some components of a SOC 2, but will not be as comprehensive. A SOC 3 is often used for early due diligence of a vendor until they are considered a serious prospect.
Final Thoughts
As we’ve seen, achieving SOC 2 compliance isn’t hard if you have the right tools and know what to fix for you to achieve it.
If you’re looking for help to achieve SOC 2 Compliance, there’s no better way than Dash. At Dash, we can help you to easily create security policies and maintain all necessary security controls with continuous compliance monitoring.